Setup security
OVERVIEW
The application allows the user to customize the security functionality for employee access within the system. The security setup contains four tabs that will be used in the customization process.
Tab 1: Create Roles
Tab 2: Create Function Groups
Tab 3: Assign Function Groups to Functions
Tab 4: Assign Function Groups to Roles
The application has a set of defaults defined for each of the four tabs. The user has the option to use the default set of job roles (tab 1) and function group names (tab 2) or to create a custom set of job roles and function group names that will best meet their business needs. All system functions (tab 3) will be assigned by default to one of the default function group names from tab 2. If the default function group names are modified, corresponding changes will need to be made to the assigned functions in tab 3. Once all functions are assigned to their appropriate function group name (tab 3), each function group name will then need to be associated with a job role (tab 4).
For the initial set up, the employee roles must be defined in the Create Roles tab. The remaining 3 tabs can use the standard defaults that come with the system until the user becomes more familiar with the application and is comfortable modifying the settings.
The Create Roles tab allows the user to define a set of roles that are applicable to that individual business. Roles are the descriptive names for each position that an employee can fill. Some examples of job roles will be manager, counterman, owner, etc.
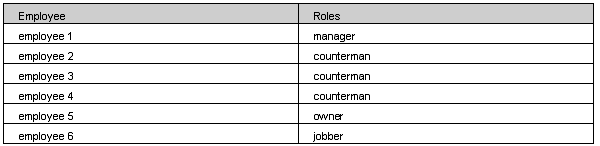
An employee can currently be assigned only one role, but there can be multiple employees falling under the same role. In the example below, employees 2,3,and 4 all fall under the same role of counterman, while employees 1,5, and 6 are the only employees filling those specific roles.
Example:

Security levels are used to help place restrictions on certain fields displayed when editing or viewing records. The application has defined pre-set fields to be restricted at a specified level. In accordance with the applications security restrictions, it is recommended to set the following security levels:
Set any system administrator role to security level of 90
Set any manager role to security level of 60
Set any standard employee role to security level of 40
The application allows the user to define which system functions should be accessed within each of the different job roles. Some examples of the system functions are: Add, Delete, Setup Tax Rates, Report Generator, Copy, etc. The Assign Function Groups to Functions tab lists many more functions that range from basic editing functions to management specific functions. All individual functions should be reviewed and logically grouped together. Each group of functions will be assigned a name by the user. Once the group names are entered in the system, each function can then be assigned to the applicable group name. The group names will later be assigned to one of the roles.
When creating a function group name (tab 2), the more specific the groups are, the more restrictive the security can be. For example, the following functions could be classified together under the General Tasks group name.
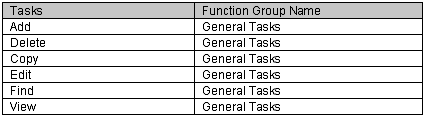
Since most employee roles would require some of the basic functions, this General Tasks group would most likely be assigned to all roles. By classifying all these editing functions together, you would inadvertently be allowing all employee roles the ability to Add and Delete. This could be avoided by assigning the functions as follows:
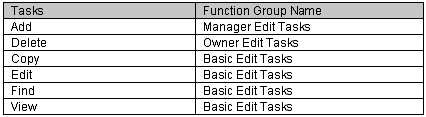
As a result, the Basic Edit Tasks group could be assigned to all roles, the Manager Edit Tasks group and the Basic Edit Tasks group could be assigned to the Manager role and all three groups could be assigned to the Owner role. Therefore, it would restrict the delete function to only be executed at an owner level.
Once a function group name is assigned to a role (tab 4), all employees falling under that role have the ability to perform any of the functions that are assigned to that function group name.
SETUP PROCESS
Steps:
Complete Worksheet
Assign a (up to) 5-digit user ID password required for initial set up
Define roles required for initial set up
Assign numeric security value required for initial set up
Review System Defaults
Review default function group name values and their corresponding functions and determine the appropriate function group name values for your business.
Enter Security Information
Enter defined roles required for initial set up
Enter numeric security value required for initial set up
Add / Modify / Delete function group name values
Assign menu functions to function group name values
Assign function group name values to each employee role